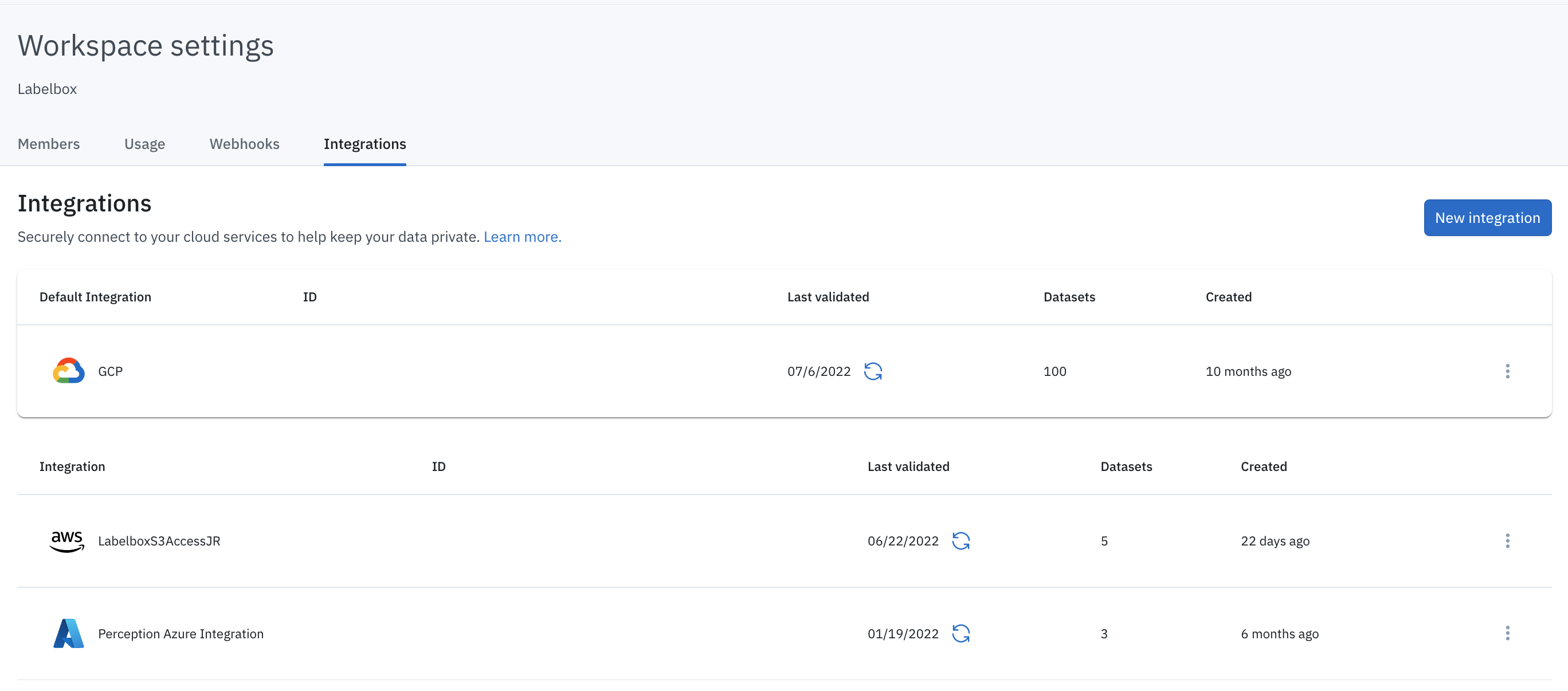
- Sign in to the Labelbox app and then select Workspace Settings from the main menu.
- Select the Integrations tab.
How IAM delegated access works
You will need to set up an IAM role in your cloud provider’s account and grant Labelbox the ability to assume that role in order to perform certain tasks on your behalf. Then, you create a policy that defines exactly what that assumed role can do. For example, Labelbox needs to be able to access assets stored in your AWS S3 bucket that you would like to label. So, you would grant the role the ability to perform GetObject requests on a particular S3 bucket (the setup instructions below will explain how to do this).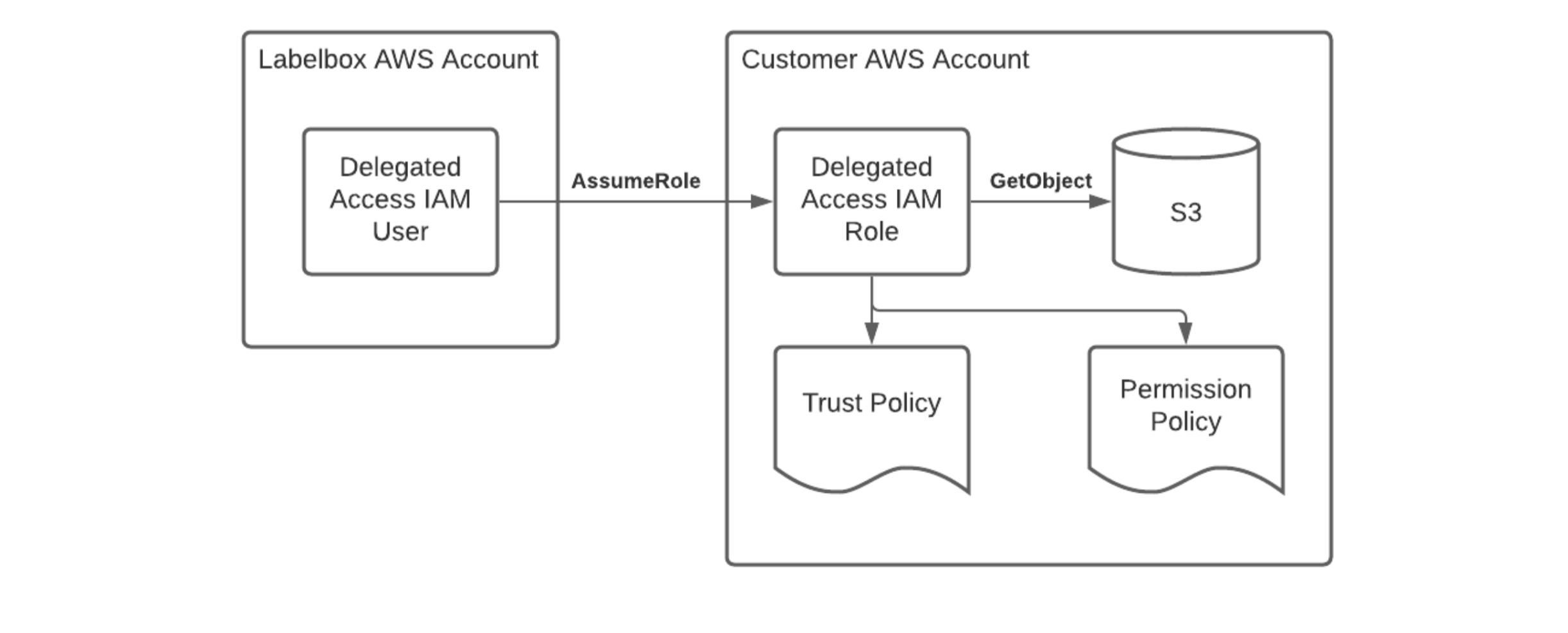
When, why, and how Labelbox accesses your data
The Labelbox app will access assets for display in the user interface (e.g., during a labeling workflow, label review, when configuring a dataset, etc). When the Labelbox app needs access to an asset, it will request an expiring, signed URL from the Labelbox API (the backend). The backend will assume the role that you configured in your AWS account and generate a signed URL for the asset being requested. The URL will then be returned to the frontend, which will use it to access the asset directly from your cloud storage: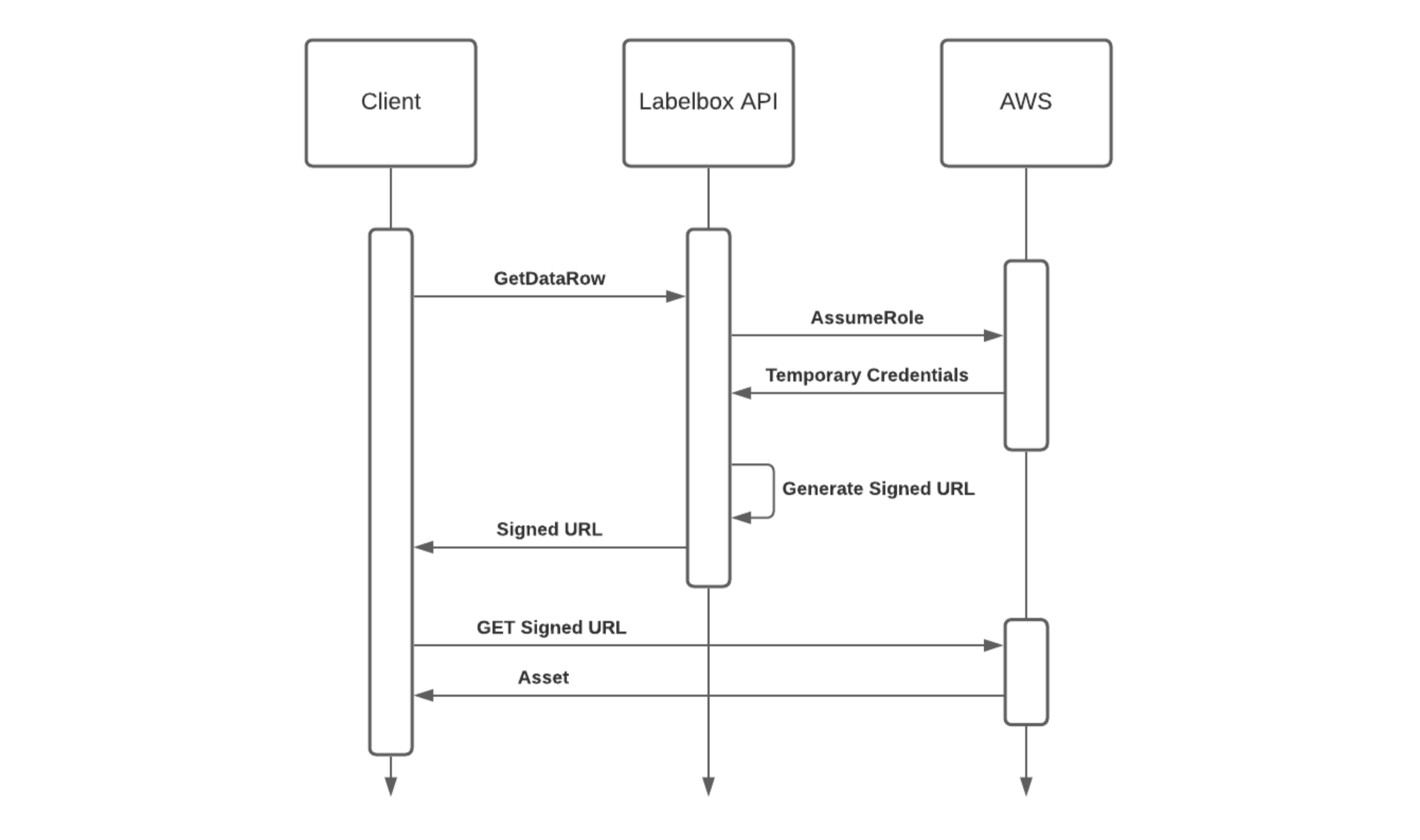
Data processing location
Currently, all asset processing is performed in US-based datacenters.Set up integration
The setup instructions vary slightly based on the cloud storage solution. Choose the setup guide that corresponds to your cloud storage provider.| Cloud storage provider | Resource |
|---|---|
| Amazon S3 | Setup guide |
| Google cloud storage | Setup guide |
| Microsoft azure blob storage | Setup guide |
Supported data types
Below are all of the asset types that you can import to Labelbox via IAM delegated access. Click on the links to see the import specifications for each data type. Note: you can also use IAM delegated access to add cloud-hosted attachments to your data rows.| Data type | Supported |
|---|---|
| Images | Import specifications |
| Video | Import specifications |
| Text | Import specifications |
| Tiled imagery (COG, NITF, GeoTIFF) | Import specifications |
| Audio | Import specifications |
| Document | Import specifications |
| Conversation | Import specifications |
View all integrations
To access the integrations menu, go to the user menu > Workspace settings > Integrations tab. You can also access your workspace settings by clicking this link: https://app.labelbox.com/workspace-settings/integrations.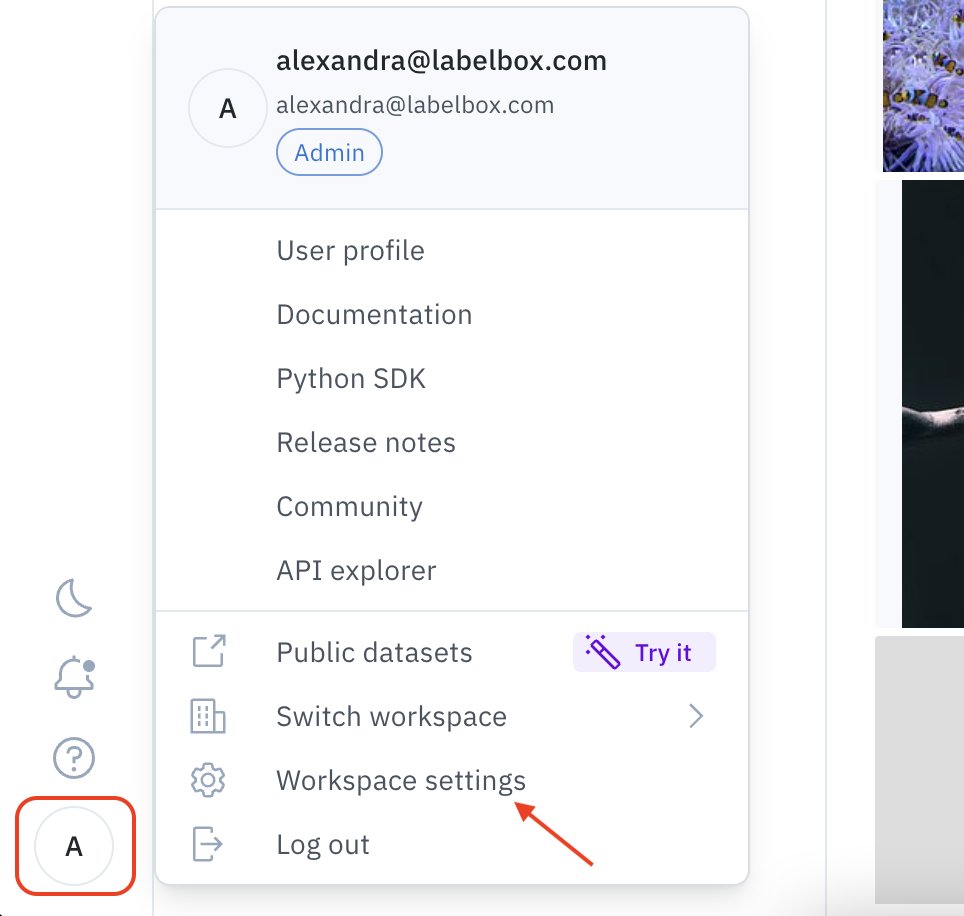
Select an integration when creating a dataset
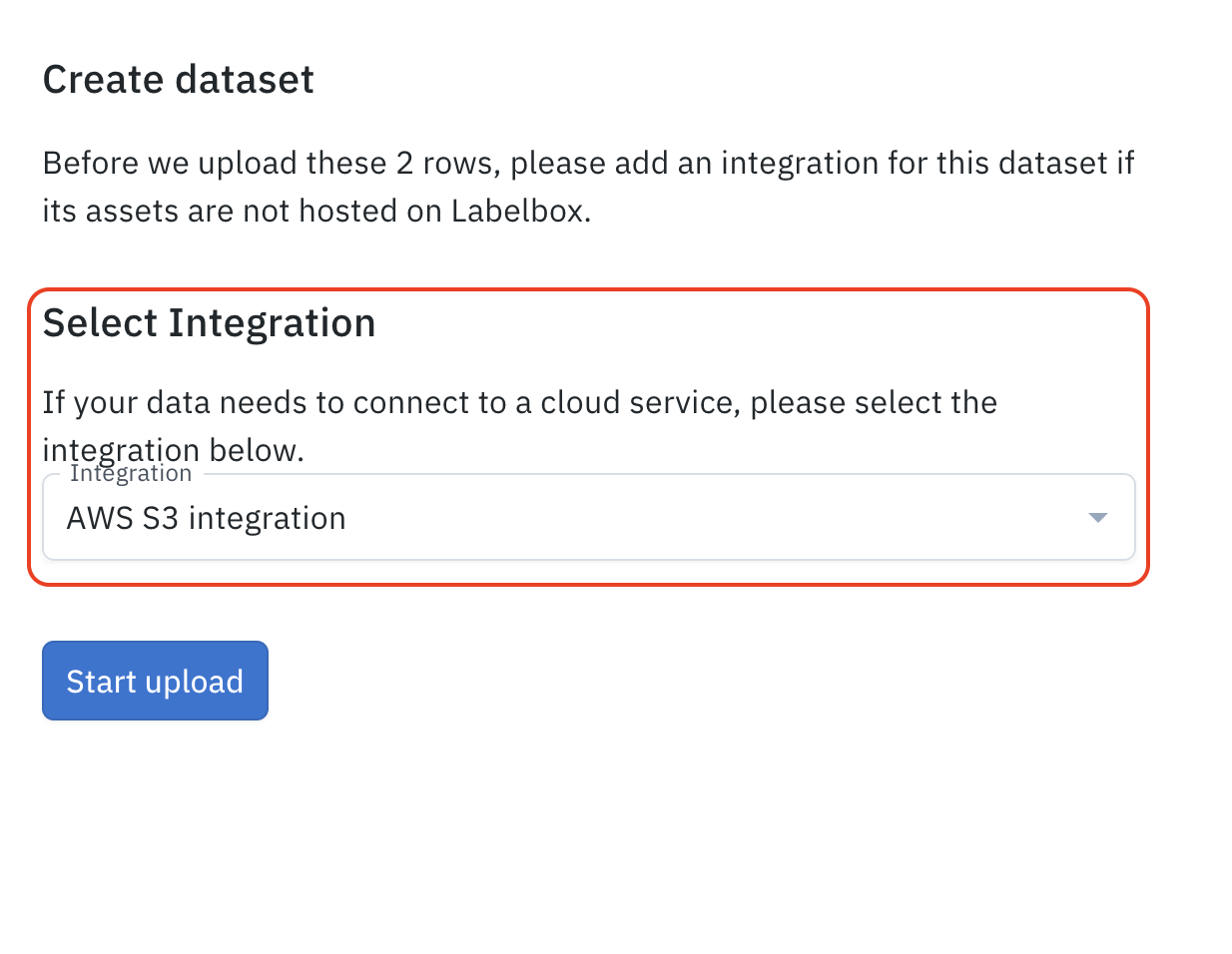
If you create a dataset via the app UI, you will have the option to select an integration for the dataset. When following these steps, please ensure that you have selected the appropriate integration or the uploads will fail.Note
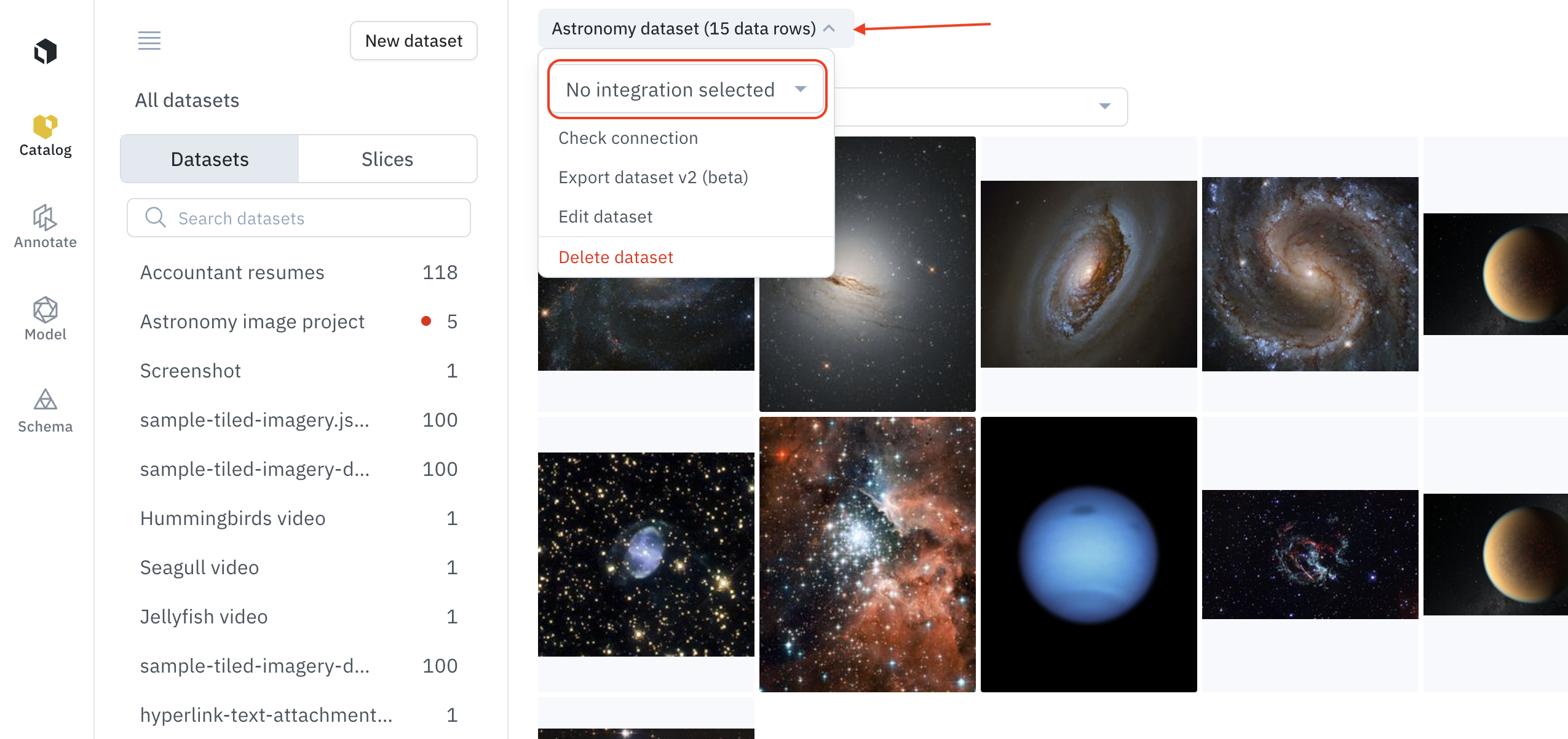
When you create a new dataset through the UI that utilizes IAM delegated access, you will be prompted to select your integration before beginning the upload.Update an integration
To update the integration linked to any dataset, regardless of how it was created, follow these steps:Admins only
Only Admins and Data admins can update integration settings on a dataset.Select an integration in the SDK
When creating a dataset via the SDK, thecreate_dataset method has an optional iam_integration parameter that can be used to specify the desired integration. Sample code for viewing and selecting integrations, along with creating a dataset using this parameter, is shown in the Common SDK methods section below.
SDK reference
For detailed Python SDK methods, checkout the referenceDelegated Access FAQ
How long are the signed URLs generated by IAM delegated access valid?
How long are the signed URLs generated by IAM delegated access valid?
Currently, the expiration time is set between 15 minutes to 24 hours depending on the selected cloud provider.
Can I invalidate all “active” signed URLs?
Can I invalidate all “active” signed URLs?
Yes, simply remove the “GetObject” permission from your AWS role’s permission policy and all active signed URLs will cease to have access to your S3 bucket.
Does Labelbox cache assets in any way?
Does Labelbox cache assets in any way?
Normally, Labelbox-hosted assets are served through a CDN to improve performance; however, Delegated Access assets are served directly from customer S3 buckets, so no CDN caching occurs.To control browser caching, you can configure various cache-related headers on your S3 bucket. See this link for details.
Can I restrict access to my assets by IP?
Can I restrict access to my assets by IP?
Yes, you might want to restrict access to your assets by only allowing requests from certain IP ranges. However, make sure to also grant the Labelbox backend access to your assets.
Does IAM delegated access affect how annotations are stored and accessed?
Does IAM delegated access affect how annotations are stored and accessed?
No, label annotations (e.g., image segmentation masks) are still stored in Labelbox-hosted storage, even when the underlying data row is customer-hosted.
Can I set up multiple IAM delegated access integrations?
Can I set up multiple IAM delegated access integrations?
It is possible to create multiple integrations. However, it is recommended to create only a single integration and make it the default. You can control what buckets to provide access to by configuring the IAM policy within the respective cloud provider.Every time you create a new dataset (via app or SDK), the Labelbox application will use the default IAM delegated access integration to access the content. This offers the best “set and forget” experience for customers who use Labelbox regularly.