Azure SSO Integration
If you’re also looking to manage user access and configure single sign-on (SSO), the Labelbox Microsoft Entra ID (Azure Active Directory) application provides an easy way to install a verified version of the Labelbox Enterprise application into your Azure tenant. For detailed steps, see the Labelbox tutorial on Microsoft Entra ID.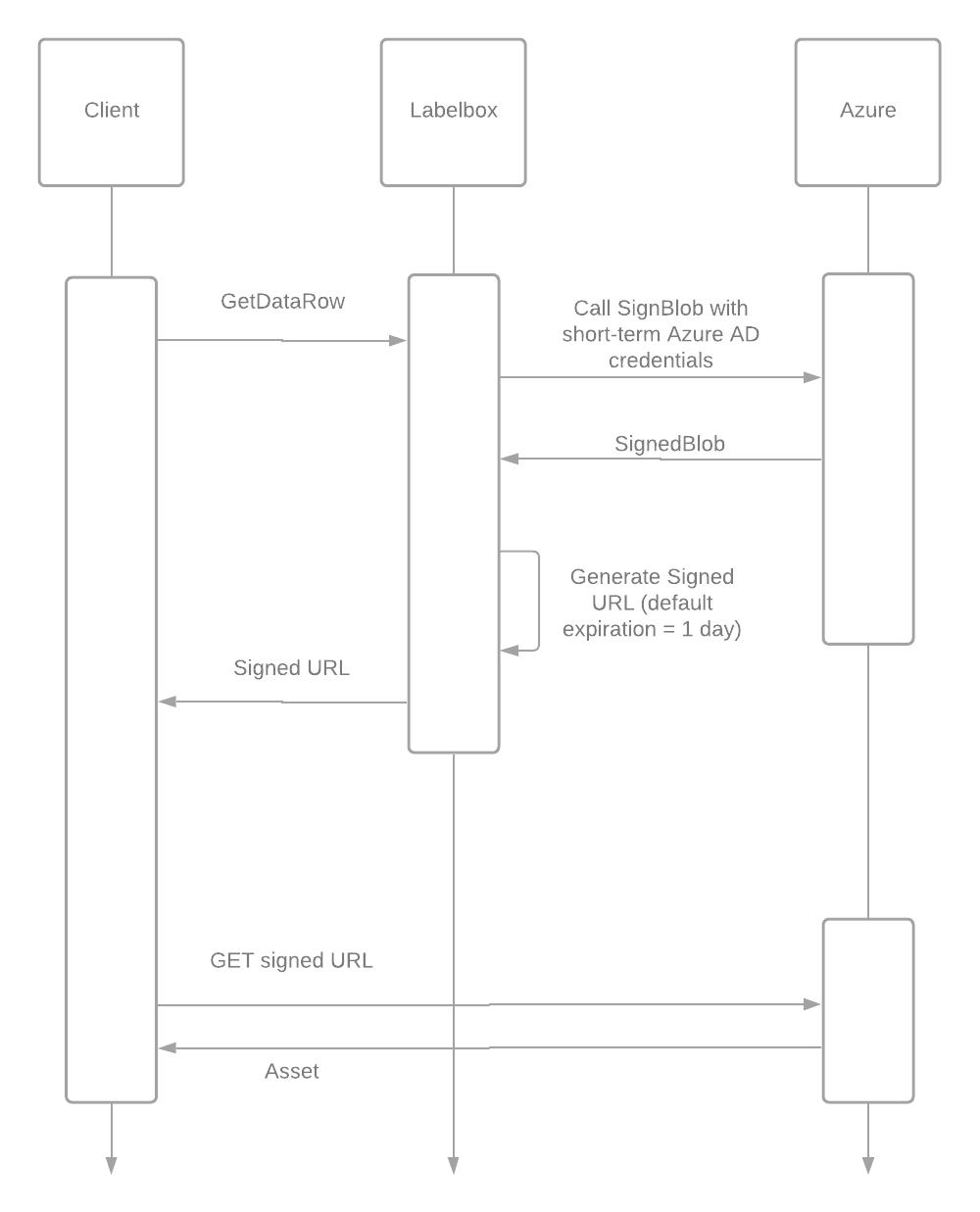
Azure Data Lake Storage
Labelbox is currently not compatible with ADLS Gen2. To set up this integration, you must use Azure Blob Storage.Step 1: Get tenant ID and container URL
First, you must get the relevant information for this integration from your Microsoft Azure account.- Navigate to your Azure blob storage container that you want to use with Labelbox.
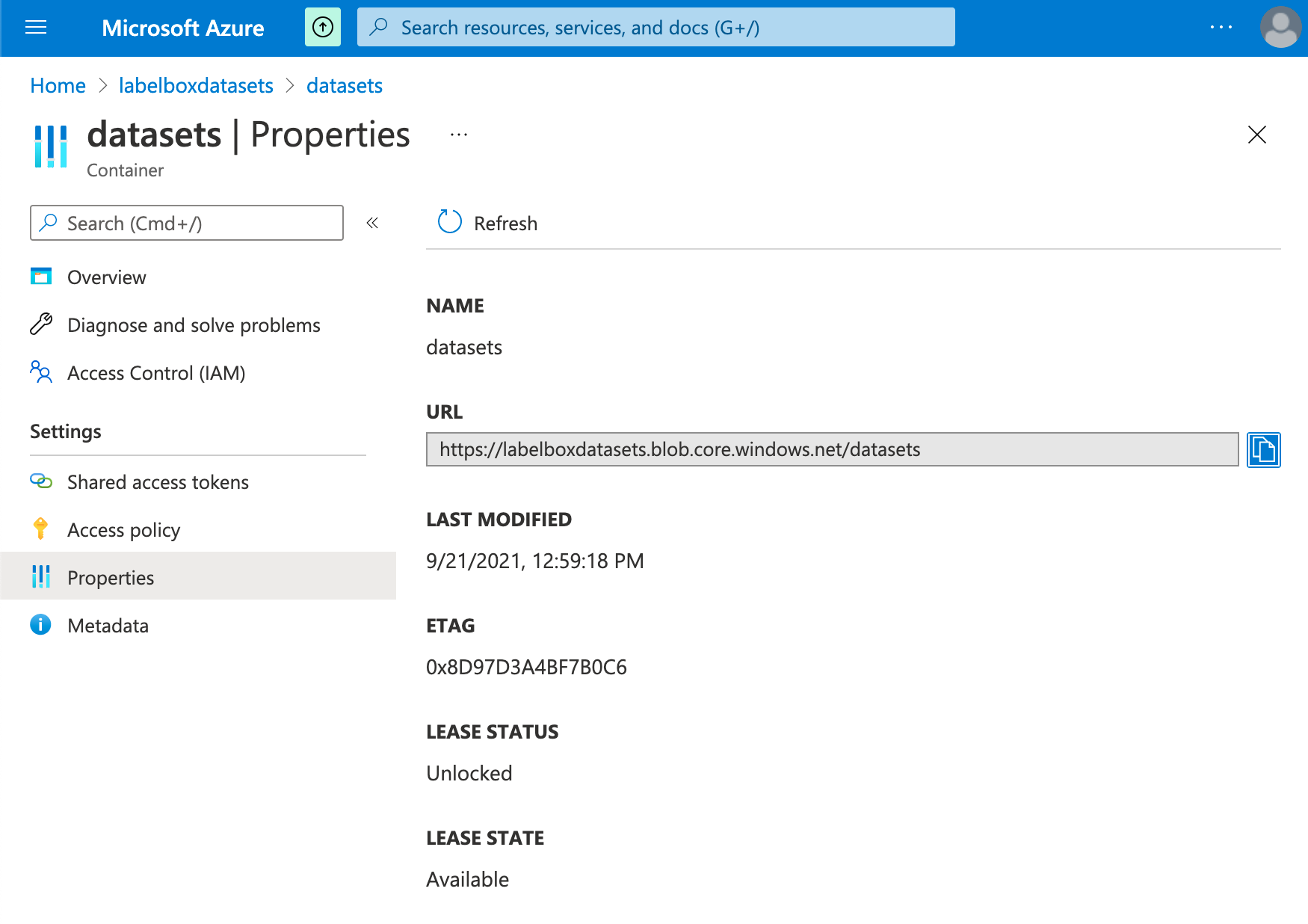
- Navigate to Azure Active Directory and select the desired tenant (Tenant ID) you want to use with Labelbox.
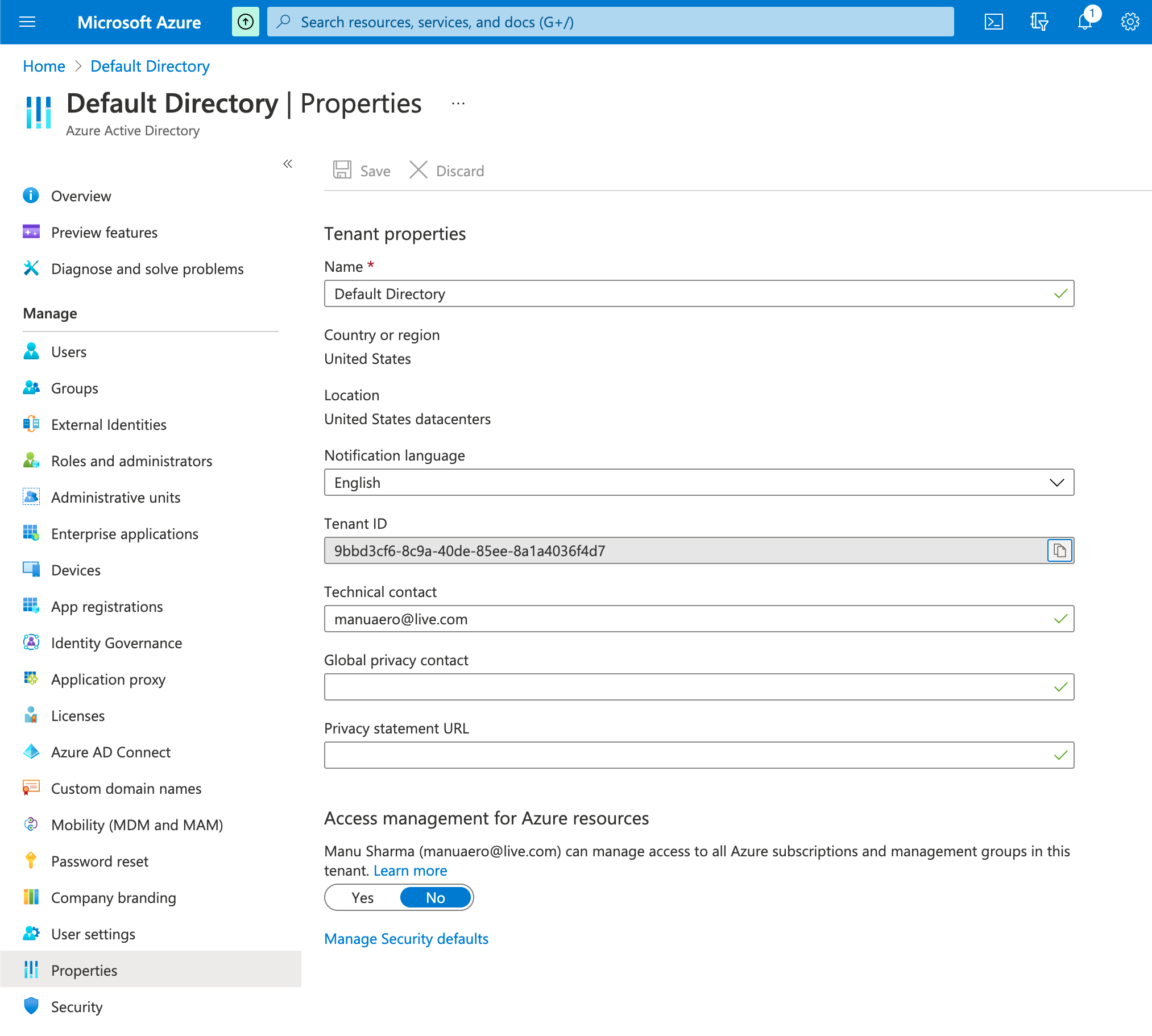
Step 2: Create Azure integration in Labelbox
Next, open up a new integration in Labelbox and input the information you gathered in the previous section.- Log into Labelbox.
- Navigate to the Integrations tab and click New integration.
- Select Microsoft Azure integration.
- Enter the details from Step 1.
- If this is your first time setting this up, please use Add Labelbox to Azure tenant to add Labelbox to your Azure tenant.
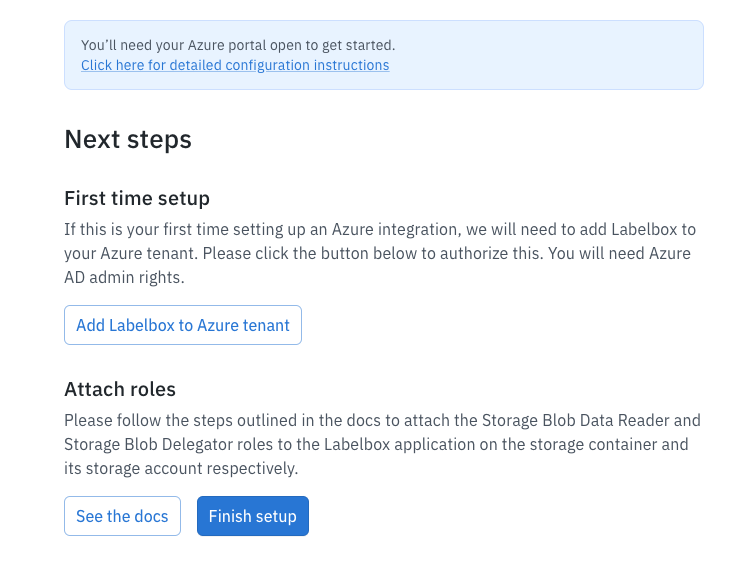
| Permissions | Resource |
|---|---|
| User.Read | Azure infra |
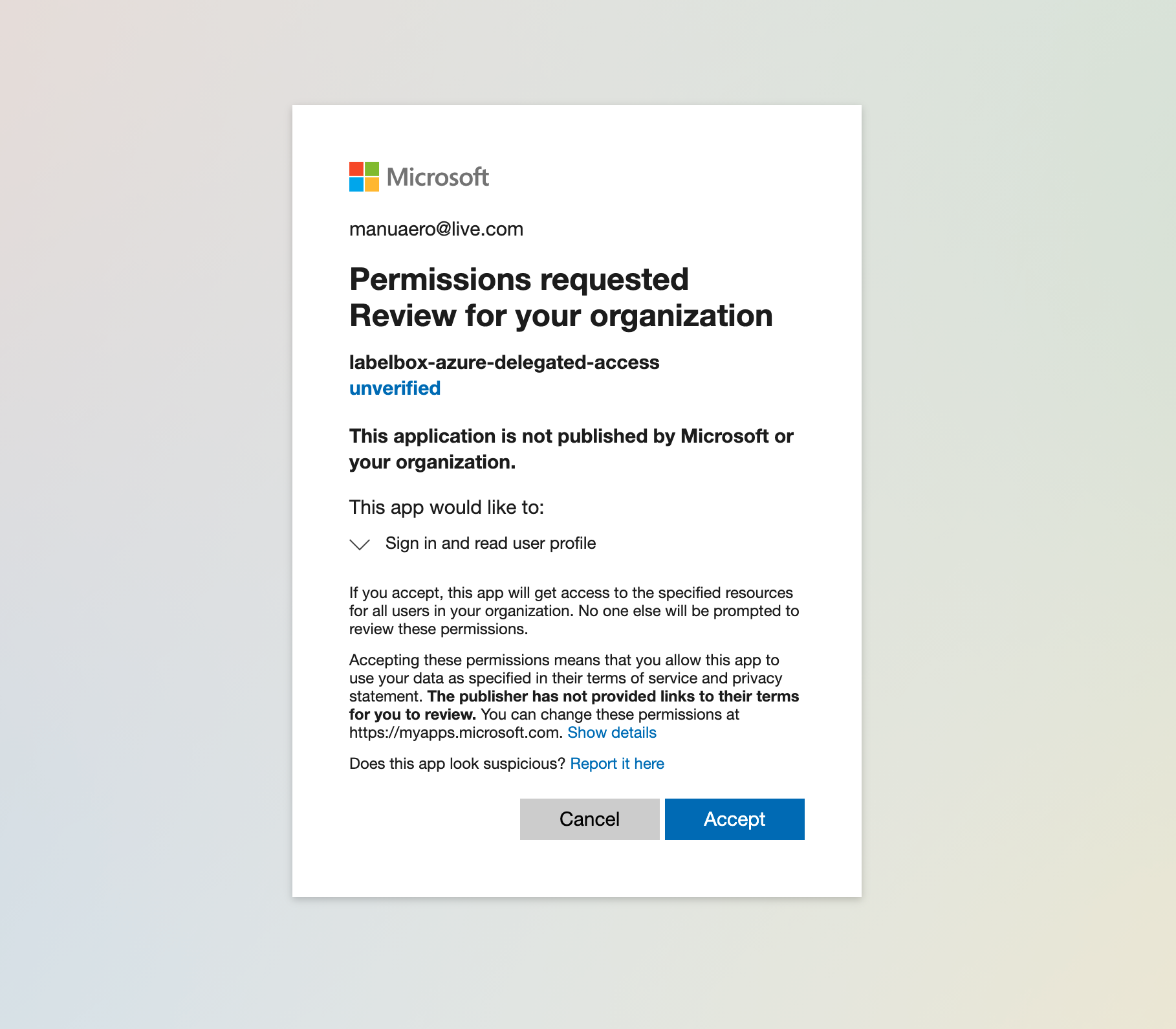
- This is a one-time operation that allows you to bind your Labebox workspace to your Azure infra.
Step 3: Grant the permissions to the Labelbox app
Now, you must assign roles to the Storage Account; container(s) will inherit its permission.| Permissions | Resource |
|---|---|
| Storage Blob Delegator | Parent Storage Account |
| Storage Blob Data Reader | Container |
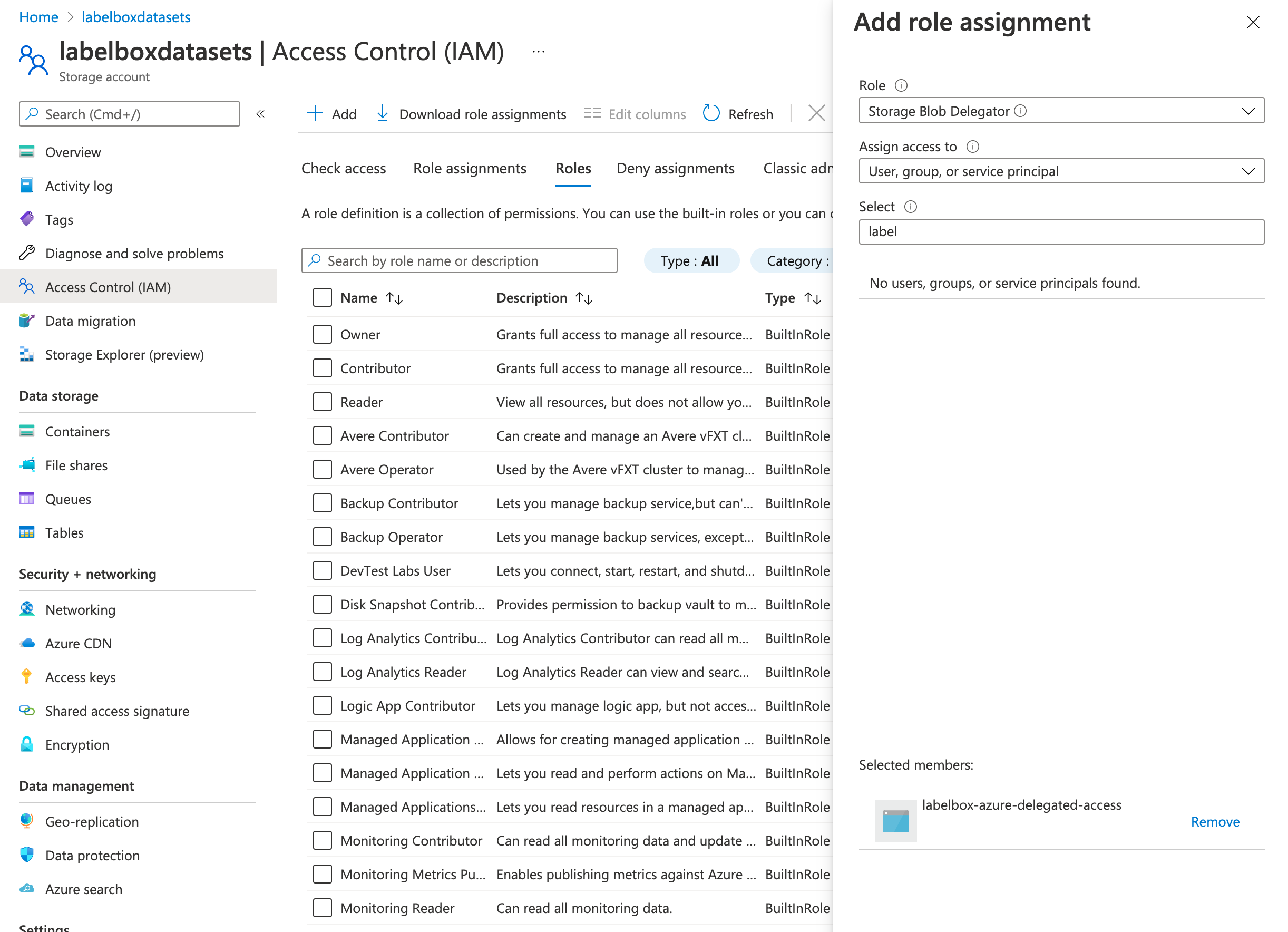
Storage Blob Delegator
- Navigate to Access Control (IAM) page within your Storage account.
- Select Add role assignment and set Role to Storage Blob Delegator, and then assign access to labelbox_azure_delegated_access app.
Storage Blob Data Reader
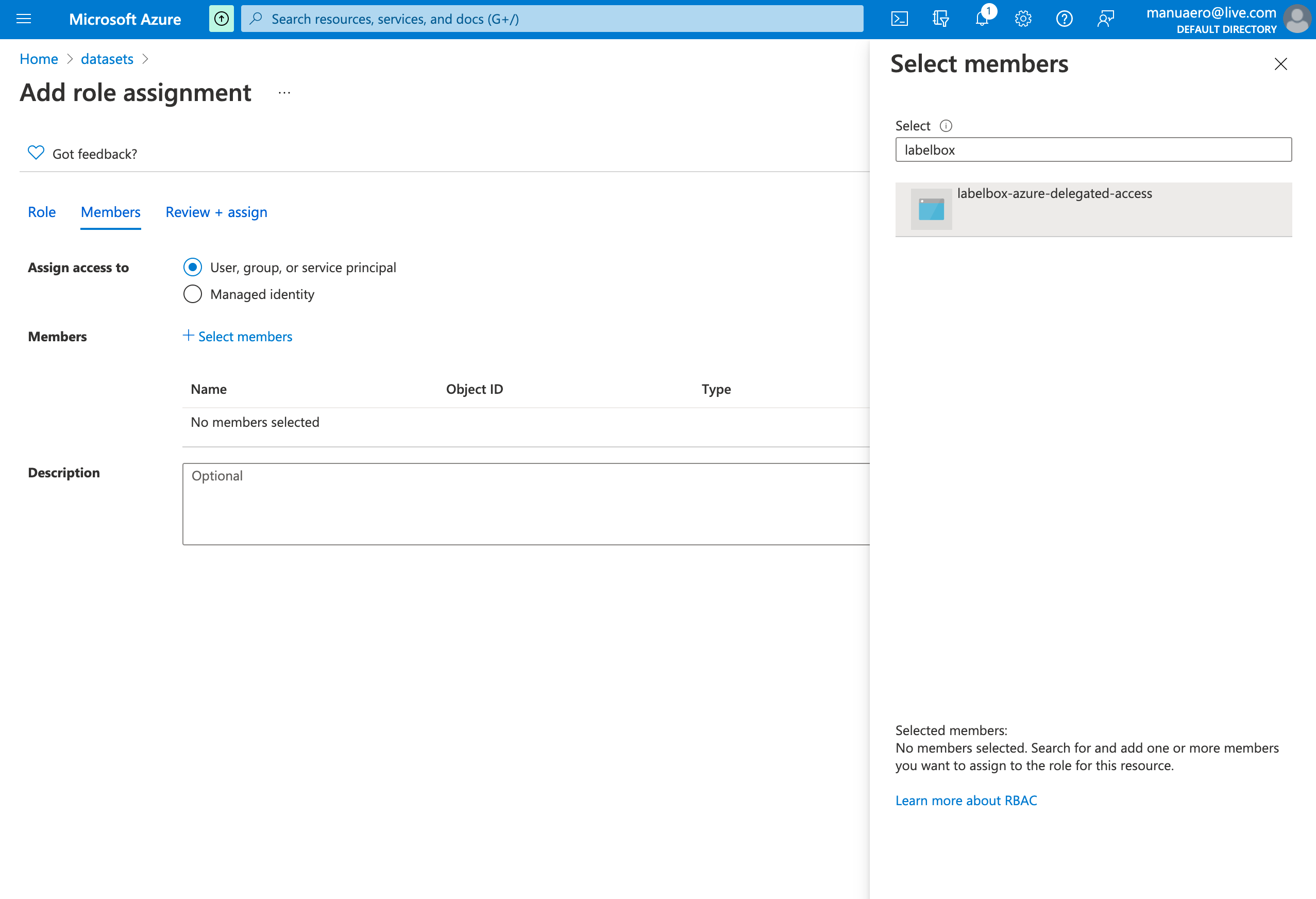
- Navigate to Access Control (IAM) page within your Container (or your Storage account).
- Click Add role assignment, Add Storage Blob Data Reader and assign to Labelbox Delegated Access app.
RBAC changes can take up to 30 mins
If you are running into any issues, such as the dataset not loading in Labelbox, it is likely that the permissions are not applied correctly. Any role-based-access-control (RBAC) changes you make can take up to 30 mins to take into effect. Learn more.Step 4: Validate the integration
In this final step, return to the Integrations tab in Labelbox and check whether the integration setup was successful.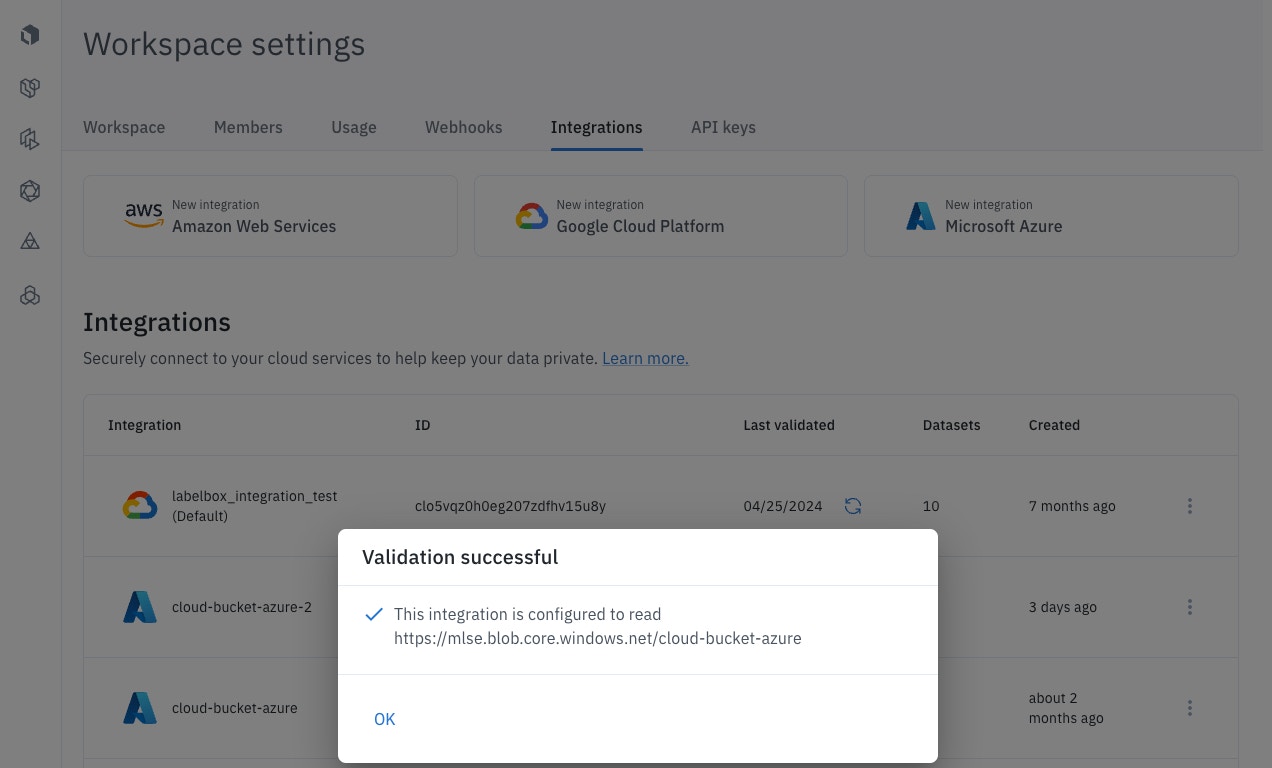
Example Azure URL
Ensure that you are using Azure URLs when creating datasets. Read Azure docs to learn how to generate blob URLs in a container (i.e: https://mlse.blob.core.windows.net/cloud-bucket-azure/image_1.jpg )Step 5: Set up CORS headers
Follow these steps to set the CORS Headers Now proceed to generate a JSON file containing Azure Blob Storage URIs.Step 6: Upload data
Now that the connection is established use the SDK to connect data to Labelbox. Click through the links below to find the import format and instructions for uploading your data type.| Data type | Supported |
|---|---|
| Images | Import specifications |
| Video | Import specifications |
| Text | Import specifications |
| Tiled imagery (COG, NITF, GeoTIFF) | Import specifications |
| Audio | Import specifications |
| Document | Import specifications |
| Conversation | Import specifications |
Additional steps
Anonymous access level
For further security, we advise that your container be set to Private to make sure no unauthorized access is possible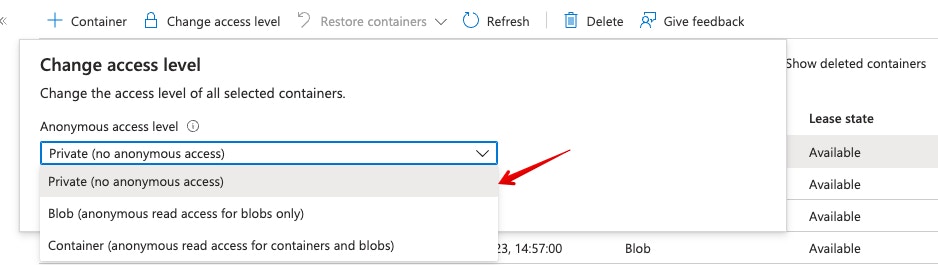
| Permissions | Resource |
|---|---|
| Anonymous access level | Container |
Networking
You can also, from the Storage account, restrict specific IP ranges to add a layer of control in your data access, if you choose to do so, make sure to include Labelbox server addresses and all the intended users who need access.- From the Storage account, go to Security + networking, Networking
- While Enabled from selected virtual networks and IP addresses is selected, you can add IP addresses that are allowed to access the Storage account and Containers
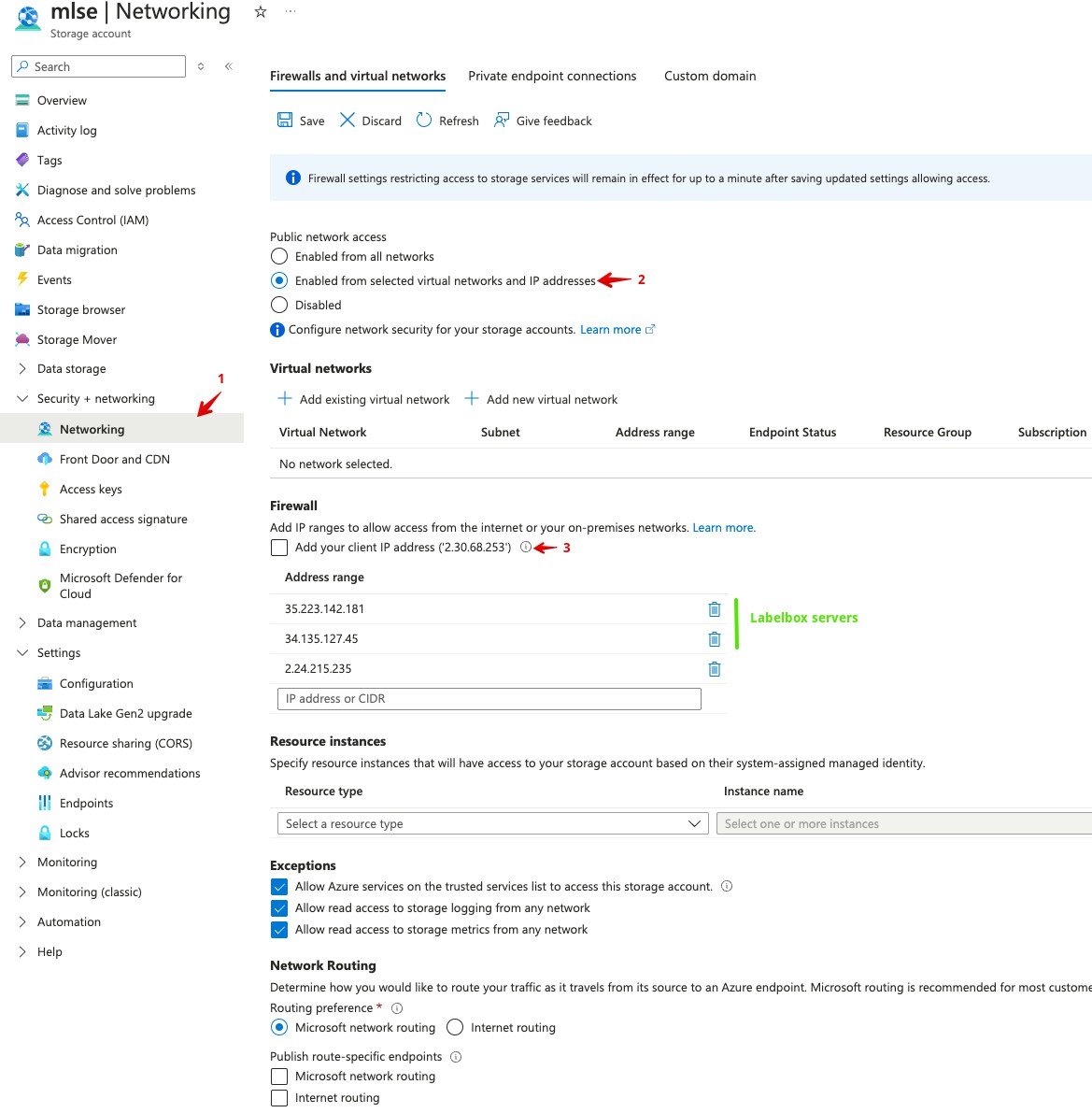
| Permissions | Resource |
|---|---|
| Grant access from an internet IP range | Storage account |